How to use IAST to prove exploitable vulnerabilities within your first-party code
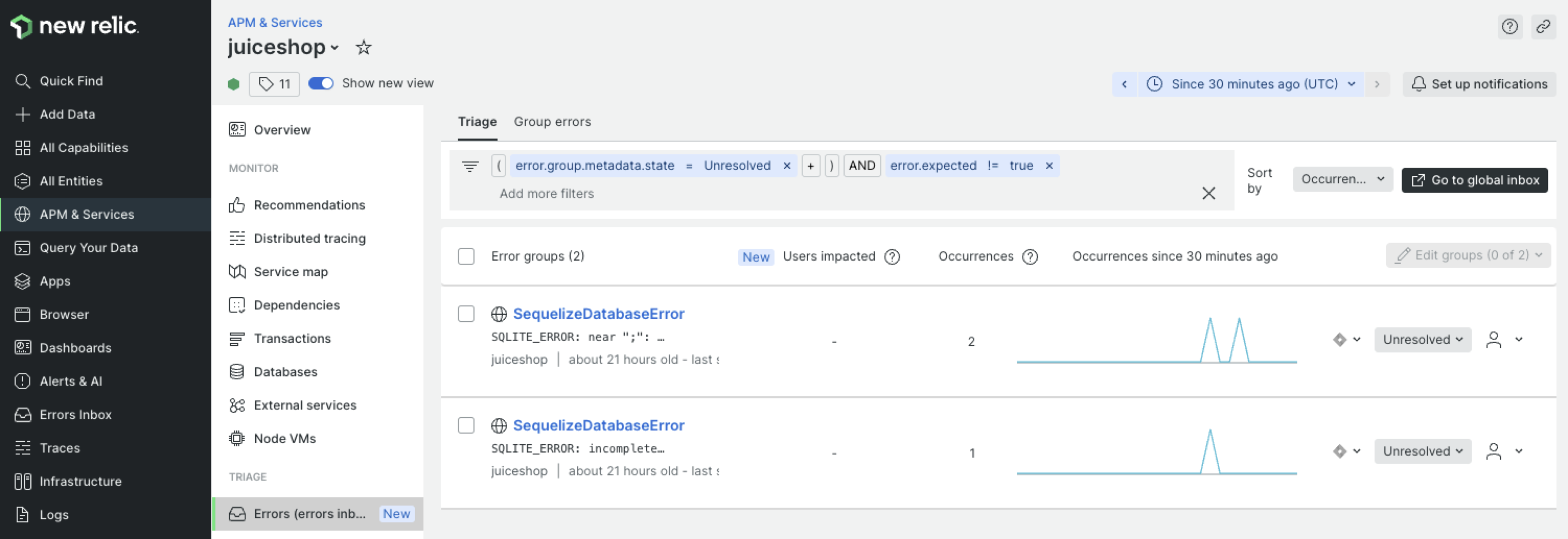
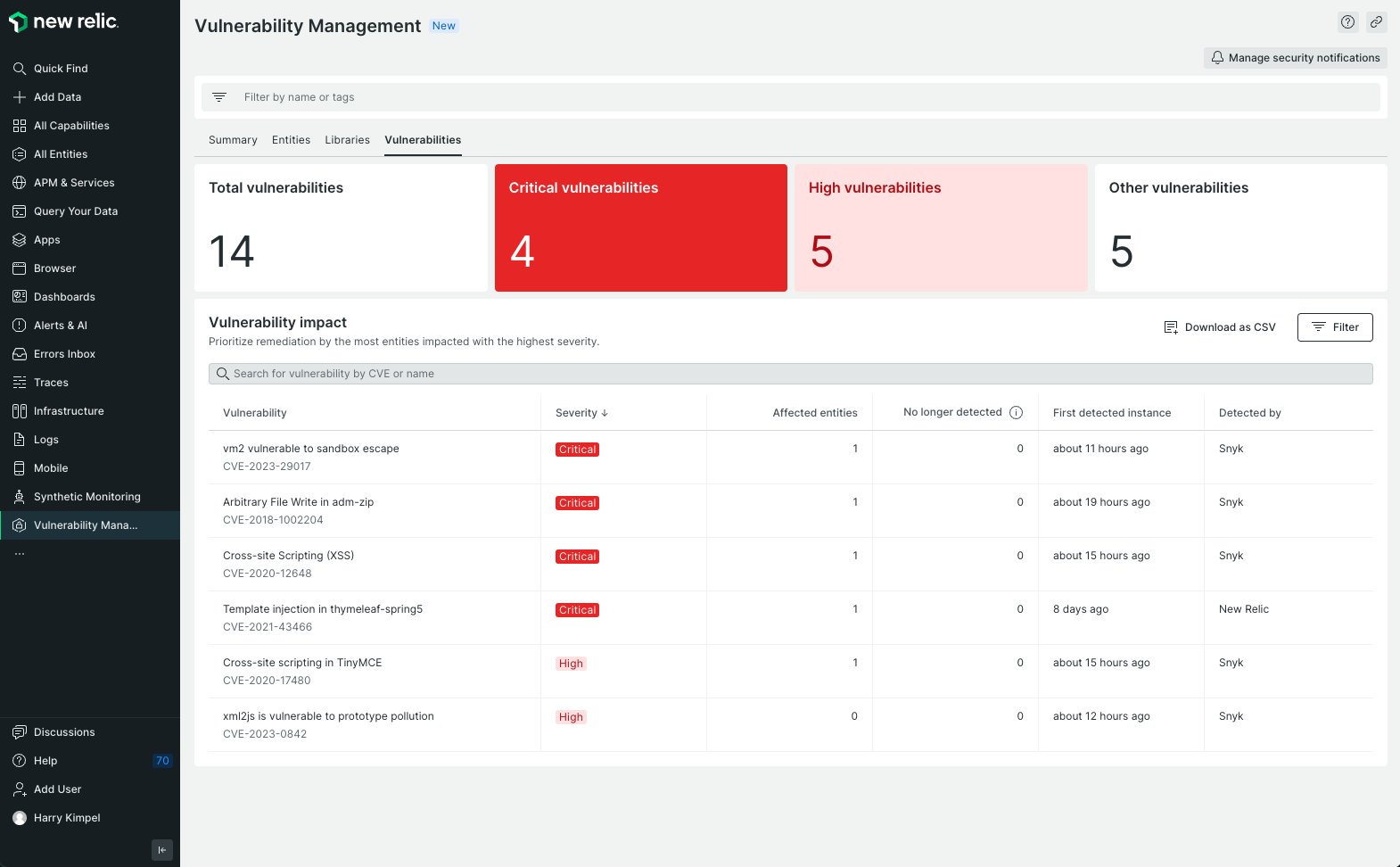
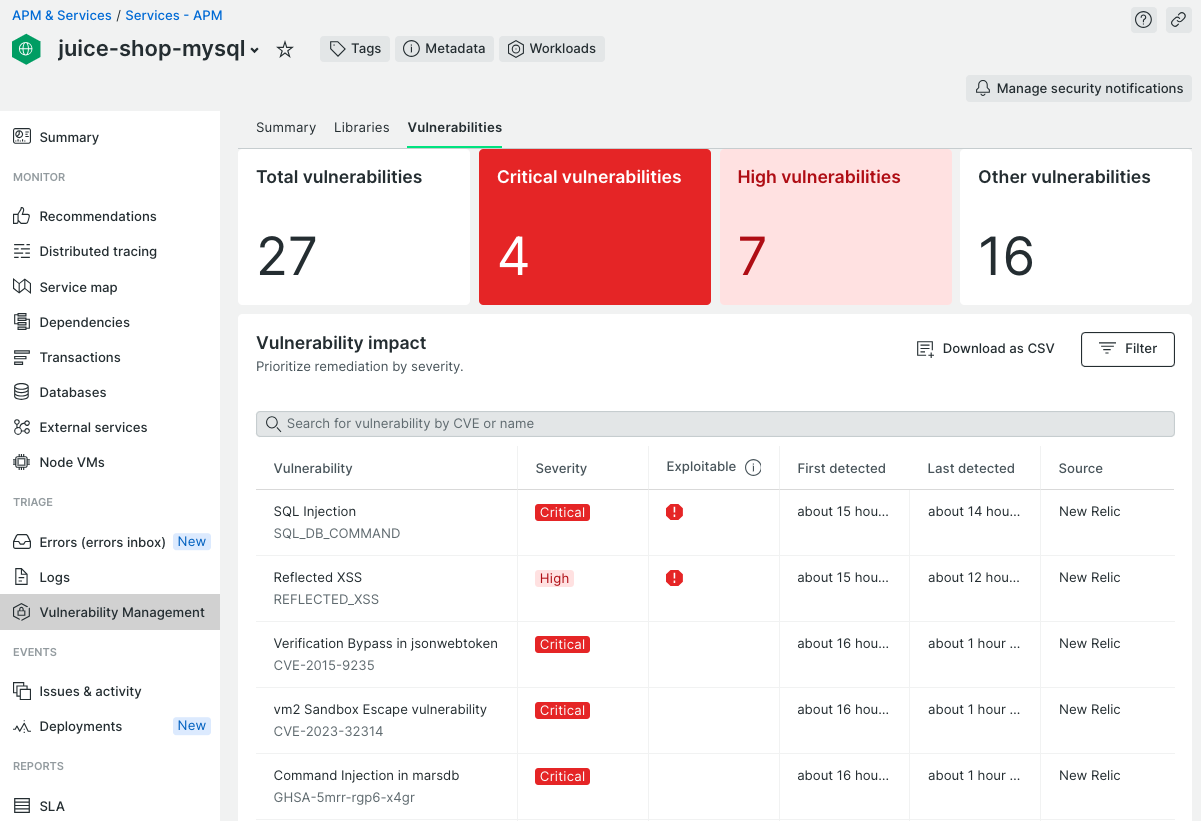
Enabling a true “shift-left” in software security by empowering DevOps and security teams to work together In some recent articles I shared how you as a developer can add security to your skillset by using New Relic capabilities. I also dug deeper into ways on how to mitigate hidden security risks of open source software libraries. Both of these blogs focused on third-party code and how it can impact the security of your software applications. In this article I will focus on the security of your own custom code, i.e. the code that you write yourself. ...