Below you will find pages that utilize the taxonomy term “Observability”
Unleashing the Power of Monitoring: Master Your WordPress with New Relic
WordPress powers countless websites across various domains, offering incredible versatility. This Content Management System (CMS) is the undisputed leader in the CMS market, powering an impressive 43.6% of all websites globally, according to these statistics. With over 810 million websites built on the platform and hundreds more launching daily (500+), its adoption continues to surge. This widespread use gives WordPress a massive 62% CMS market share, significantly outpacing its rivals.
However, even the most robust WordPress sites can face performance challenges. Slowdowns are often caused by factors such as slow-loading plugins, database connection issues, infrastructure capacity problems, network trouble, large page assets (like images or fonts), and broken links. This is why robust monitoring is essential for maintaining a fast, reliable, and user-friendly website.
Optimizing Kafka Tracing with OpenTelemetry: Boost Visibility & Performance
Ideally, you should be using distributed tracing to trace requests through your system, but Kafka decouples producers and consumers, which means there are no direct transactions to trace between them. Kafka also uses asynchronous processes, which have implicit, not explicit, dependencies. That makes it challenging to understand how your microservices are working together.
However, it is possible to monitor your Kafka clusters with distributed tracing and OpenTelemetry. You can then analyze and visualize your traces in an open-source distributed tracing tool like Jaeger or a full observability platform like New Relic. In this post, I will leverage a simple application to show how you can achieve this.
Why I'm Excited for .NET Conf 2024
Greetings fellow .NET enthusiasts and tech aficionados! With the highly-anticipated .NET Conf 2024 just around the corner, I find myself reflecting on how far we’ve come in the world of .NET development and what thrilling innovations are yet to come.
A Journey Through .NET
Let’s take a quick stroll down memory lane. My experience with .NET technologies dates back to 2002, when I first dipped my toes into the vast sea of possibilities offered by .NET. Over the years, I’ve seen it transform from a promising framework into a powerhouse that underpins countless applications worldwide. Every upgrade has brought something new and exciting, fueling my passion for staying on the cutting edge of technology.
Observability as code for AI apps with New Relic and Pulumi
AI applications are complex and distributed, making effective monitoring challenging. Combining the New Relic intelligent observability platform with Pulumi’s infrastructure-as-code and secret management solutions allows for an end-to-end “observability as code” approach. This method enables teams to:
- Define artificial intelligence (AI) and large language model (LLM) monitoring instrumentation along with cloud resources programmatically.
- Securely manage API keys and cloud account credentials.
- Automatically deploy New Relic instrumentation alongside AI applications and infrastructure.
Benefits include:
How To Observe Your Blazor WebAssembly Application With OpenTelemetry And Real User Monitoring
Effortless integration and enhanced visibility with OpenTelemetry in Blazor WebAssembly
Challenges in observing WebAssembly applications
Observing WebAssembly applications presents unique challenges that stem from its design and execution environment. Unlike traditional web applications, where monitoring tools can hook directly into JavaScript and the Document Object Model (DOM), WebAssembly runs as binary code executed within the browser’s sandbox. This layer of abstraction complicates direct introspection, as traditional monitoring tools are not designed to interact with the lower-level operations of WebAssembly. The Bytecode Alliance plays a crucial role here, promoting standards and tools that aim to enhance the security and usability of WebAssembly, including better support for observability. Moreover, the performance characteristics of WebAssembly, which can closely approach native speeds, demand monitoring solutions that are both highly efficient and minimally invasive to avoid impacting the user experience. This creates a complex scenario for developers who need detailed visibility into their applications’ behavior without sacrificing performance.
Guide: How to route Docker logs correctly in New Relic
Streamlining Container Log Management for Clarity and Control
Hello, New Relic aficionados! Picture this: you’re at a bustling local user group meetup, exchanging ideas and sharing tech stories. Amidst the animated discussions and clinking coffee cups, a fellow developer—let’s call him Alex—shares a frustrating puzzle. Alex’s Docker Compose applications are acting like rebellious teenagers, sending their logs to the New Relic Host UI instead of their designated New Relic Container UI. As you dive deeper into the problem, a light bulb goes off. This isn’t just Alex’s struggle; it’s a common snag affecting many of us in the Docker and New Relic community.
A Deep Dive into Zero-Day Vulnerability Alerts with New Relic APM
Empowering Developers with Real-Time Security Insights and Proactive Vulnerability Management
Amidst the ever-evolving landscape of cybersecurity, the recent revelation of a zero-day vulnerability in Fortinet’s FortiOS serves as a stark reminder of the constant cat-and-mouse game between defenders and attackers.
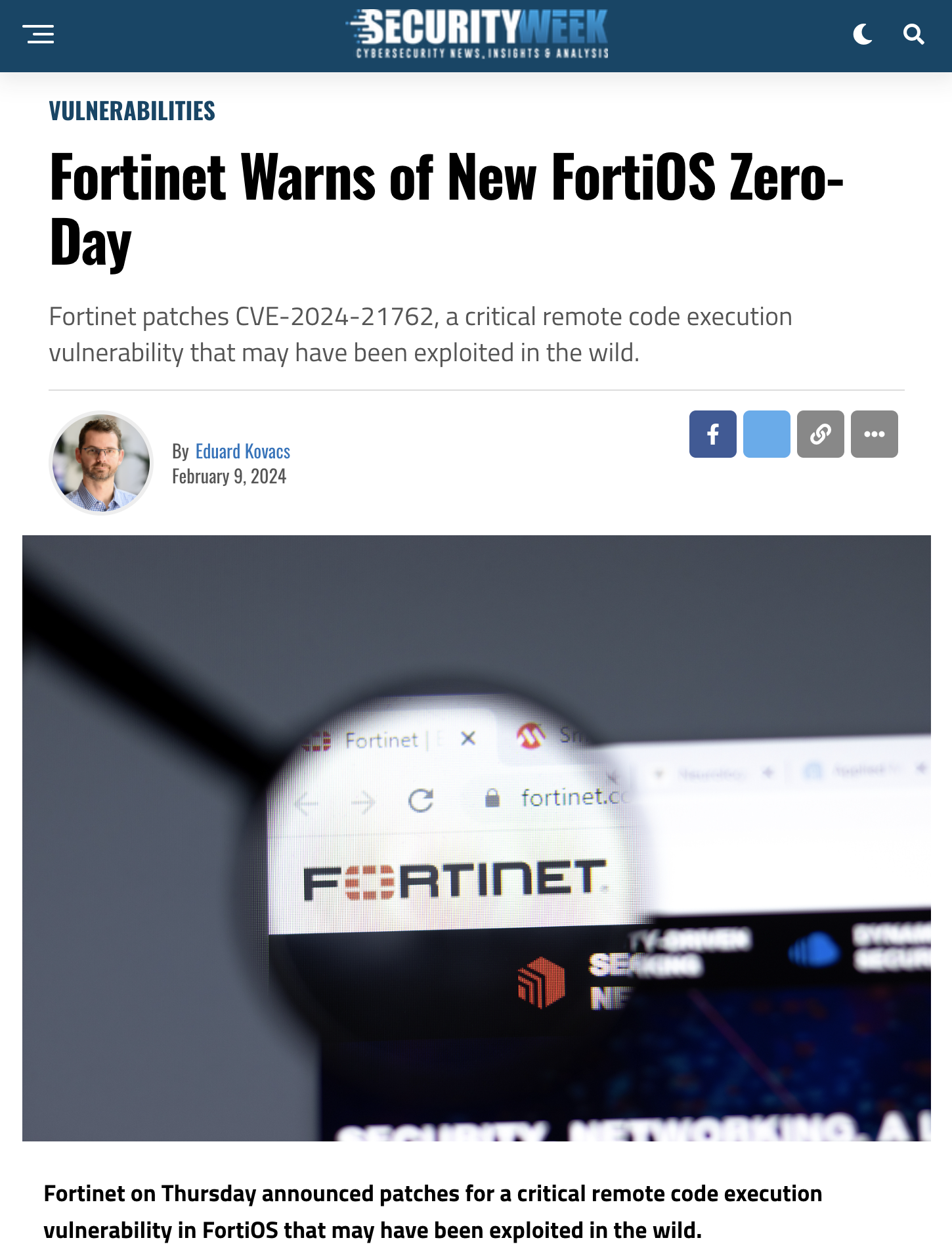
Staying ahead of potential security threats isn’t just a best practice; it’s a necessity. For developers, the challenge lies not only in identifying vulnerabilities but in doing so proactively, especially when it comes to zero-day exploits. In this blog post, we’ll explore how New Relic application performance monitoring (APM) empowers developers to create zero-day vulnerability alerts, offering a robust solution to enhance security postures without the need for extensive scanning.
Using .NET Aspire eShop application to collect all the telemetry
Learn how to collect all the telemetry from the .NET Aspire eShop application and send it to an OpenTelemetry backend such as New Relic

.NET Aspire is the new kid on the block when it comes to an opinionated, cloud-ready stack for building observable, production-ready, distributed applications. Having a built-in dashboard for the monitoring data is nice during development. But how do you configure OpenTelemetry correctly to send it to an observability backend? This is what this blog post is all about. And you’ll also learn how to send custom attributes by leveraging OpenTelemetry SDKs.
How to monitor Microsoft 365: Observing AD FS
A practical guide to Active Directory Federation Services for a resilient Microsoft 365 ecosystem
In our previous blog on how to monitor Microsoft 365 (M365), we delved into service overviews and the critical importance of synthetic user login monitoring. In this blog, we set our sights on a core component that forms the backbone of secure identity and access management: Active Directory Federation Services (AD FS).
As organizations increasingly migrate their operations to the cloud, ensuring the robustness of identity and authentication mechanisms becomes paramount. AD FS plays a pivotal role in this landscape, acting as the linchpin for seamless and secure single sign-on (SSO) experiences within the M365 ecosystem.
How to use CodeStream—and shift left your observability practice
Your adventure in the world of observability, performance optimization, and security begins here.
In the fast-paced world of software development, the quest for smoother, more efficient applications feels like a never-ending adventure. But in this adventure, it’s not about slaying dragons or uncovering hidden treasures; it’s about ensuring your code performs seamlessly and your users are happy.
As a developer, I’ve faced the challenges of reactive observability, where we typically identify and resolve issues only after they’ve disrupted our applications. It’s a scenario that’s all too familiar for many of us. Adding New Relic CodeStream to your tool inventory can help rescue your team from a perilous fate and bring their observability game to a new level.
How to monitor Microsoft 365: Getting started
One of the most popular and widely adopted business tool suites is Microsoft 365 (previously known as Microsoft Office 365) or just M365 for short. M365 offers a comprehensive array of applications and services, including email, document collaboration, video conferencing, and more, all hosted on the cloud. M365 provides numerous benefits in terms of flexibility and accessibility, but it also introduces new security, performance, and compliance challenges. This is why monitoring M365 applications is critically important for organizations of all sizes. Monitoring M365 applications is essential in helping businesses maintain a secure, efficient, and compliant digital environment.
How to use IAST to prove exploitable vulnerabilities within your first-party code
Enabling a true “shift-left” in software security by empowering DevOps and security teams to work together
In some recent articles I shared how you as a developer can add security to your skillset by using New Relic capabilities. I also dug deeper into ways on how to mitigate hidden security risks of open source software libraries. Both of these blogs focused on third-party code and how it can impact the security of your software applications. In this article I will focus on the security of your own custom code, i.e. the code that you write yourself.
Mitigate the hidden security risks of open source software libraries
Check your source code for any vulnerable libraries and start mitigating these issues
Open source software libraries have become an integral part of modern software development. They are widely used by developers to accelerate the development process and reduce costs. On average, open source libraries make up 70-90% of an entire software application. However, the use of open source libraries also comes with hidden security risks that could potentially harm your organization’s reputation and financial well-being.
Level up your security skillset with New Relic
Not every developer is a security expert, but use these tips to improve your skills
In today’s digital age, security is a major concern for individuals and organizations alike. With the increasing number of cyber-attacks and data breaches, it’s crucial for developers to have a thorough understanding of security best practices. The security of an application is of the utmost importance, as it can directly impact the safety and privacy of users’ data.
Updated Snyk Webhook Integration with New Relic
In a recent post I wrote about the ability to send all your application security vulnerabilities found by Snyk directly to your New Relic observability platform.
Now, New Relic made it even easier to achieve that by providing a dedicated security ingest processor that ‘understands’ the payload from a Snyk webhook. All the details on how to get started, create and configure a Snyk webhook to send into your New Relic account is provided in this docs page: https://docs.newrelic.com/docs/vulnerability-management/integrations/snyk/
How to send Snyk vulnerability data to the New Relic observability platform
Security and observability data go hand in hand when it comes to application health. If you can put those two sources of data behind a single pane of glass you can make your life a lot easier. By leveraging the different options that the Snyk platform provides, you can send all your application security vulnerabilities found by Snyk directly to your New Relic observability platform. Let’s see how!
Prerequisites
Here are all the necessary links to get started:
Forward Snyk Vulnerability data to Splunk Observability Cloud
TL;DR
Leverage a Prometheus Exporter to send all your application security vulnerabilities from Snyk into Splunk.
Here are all the necessary links to get started:
- Snyk Exporter: https://github.com/lunarway/snyk_exporter
- Splunk OpenTelemetry Collector for Kubernetes: https://docs.splunk.com/Observability/gdi/opentelemetry/install-k8s.html#otel-install-k8s
Update (2022-09-22)
The option that I am describing here is just one way to achieve this. There might even be a more straight forward option available that I started to describe in a more recent post. Please find an additional approach in my post Snyk Integration Capabilities with WebHooks - some examples.
Observing Dapr applications with New Relic One
It was back in 2019 at Microsoft Ignite in Orlando when I discovered a new project referred to as Distributed Application Runtime, or Dapr for short. This immediately caught my attention and Mark Russinovich did an amazing job presenting this to the audience.
Dapr is quite an interesting project for me in many ways. First of all, software architecture is near and dear to my heart and Dapr solves a lot of the challenges developers typically face when designing and implementing applications. Its portable, event-driven runtime makes it easy for developers to build resilient, stateless and stateful microservices applications that run on the cloud or edge and embraces the diversity of languages and developer frameworks.
How-To: Set-up New Relic to observe Dapr and it's applications
How-To: Set-up New Relic to collect and observe metrics, traces and logs from Dapr and the underlying applications.
Enable Dapr metrics and logs with New Relic Kubernetes integration for Azure Kubernetes Service (AKS) and application traces using OpenTelemetry.
Prerequisites
- Azure Kubernetes Service
- kubectl
- An installation of Dapr on Kubernetes
- Perpetually free New Relic account, 100 GB/month of free data ingest, 1 free full access user, unlimited free basic users
Enable New Relic Kubernetes integration
The Kubernetes integration monitors worker nodes. In Azure Kubernetes Service, master nodes are managed by Azure and abstracted from the Kubernetes platforms.