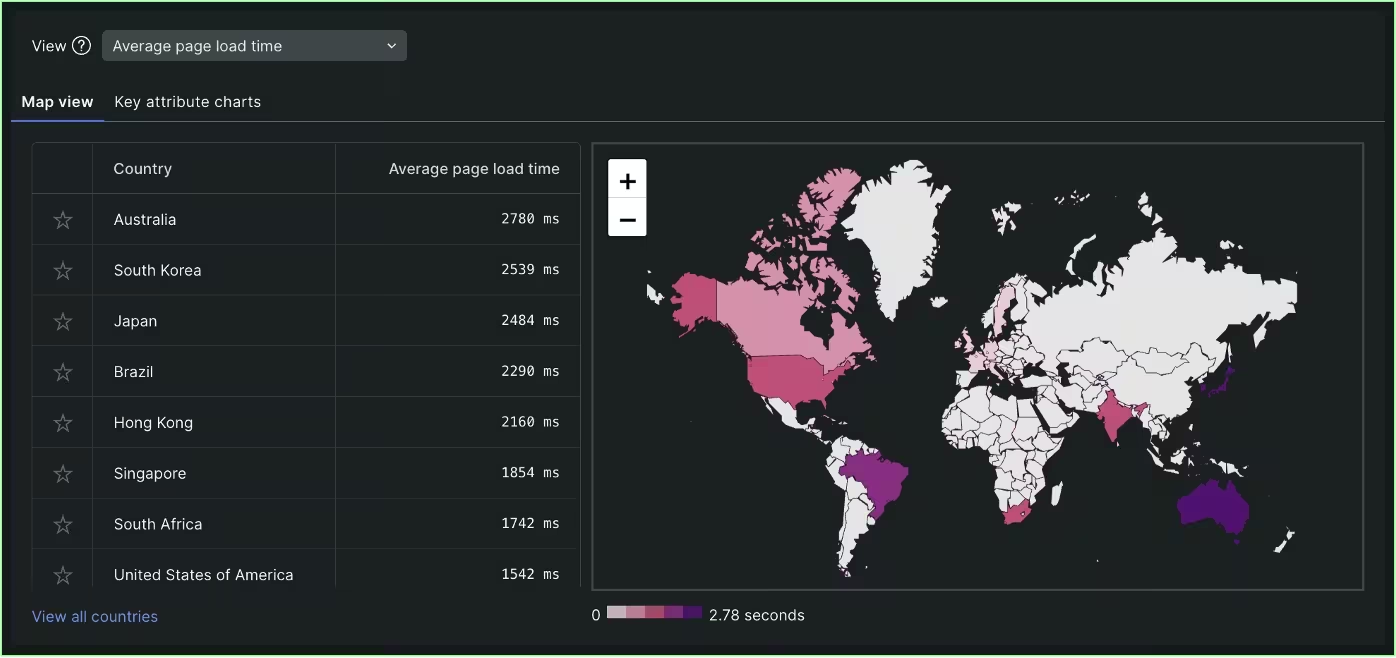
Unleashing the Power of Monitoring: Master Your WordPress with New Relic
WordPress powers countless websites across various domains, offering incredible versatility. This Content Management System (CMS) is the undisputed leader in the CMS market, powering an impressive 43.6% of all websites globally, according to these statistics. With over 810 million websites built on the platform and hundreds more launching daily (500+), its adoption continues to surge. This widespread use gives WordPress a massive 62% CMS market share, significantly outpacing its rivals. However, even the most robust WordPress sites can face performance challenges. Slowdowns are often caused by factors such as slow-loading plugins, database connection issues, infrastructure capacity problems, network trouble, large page assets (like images or fonts), and broken links. This is why robust monitoring is essential for maintaining a fast, reliable, and user-friendly website. ...